Published on July 20th 2024 | 11 mins , 2142 words
Kenya Certificate of Secondary Education (K.C.S.E)
NAME
INDEX NO
SCHOOL
SIGNATURE
DATE
451/1
COMPUTER STUDIES PAPER 1
(THEORY)
JULY/AUGUST 2024
TIME: 2 ½ HOURS
Instructions to Candidates
(a)Write your name and admission number in the spaces provided above.
(b)This Paper consists of two sections A and B.
(c)Answer ALL the questions in section A.
(d)Answer question 16 (compulsory) and any other three questions from section B.
(e)All answers should be written in the spaces provided.
(f) This paper consists of 12 printed pages. Candidates should check to ensure that all pages are printed as indicated and no questions are missing
SECTION A:
ANSWER ALL THE QUESTIONS IN THE SPACES PROVIDED
1. Describe three component of a spreadsheet functions (3mks)
Equal sign(=)mark the beginning of a function
Function Name describe the activity to be performed
Arguments- the range of value to be acted upon
2. (a) Identify the devices labeled A and B.
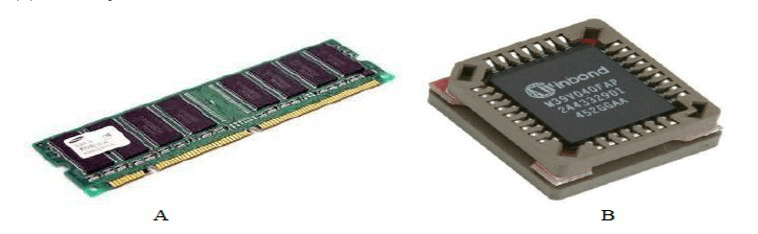
B - CPU
(b) Identify two characteristic of device labeled A . (2mks)
It is volatile
It is directly accessible by the CPU
Has limited storage capacity
Holds processes currently undergoing execution by the CPU or awaiting execution
Data stored in RAM is accessed/retrieved randomly
3. Describe 3 functions of repeaters. (3mks)
Regenerates/reconstructs data signals
Amplifies data signals
Extends network distance
Re-transmit data signals
4. Convert the following binary number 1101.012 to decimal. (2mks)
\((1 \times 2^{3})\) + \((1 \times 2^{2})\) + \((0 \times 2^{1})\) + \((1 \times 2^{0})\)+\((0 \times 2^{-1})+ (1 \times 2^{-2}) \)
8+4+1+0.25=\(13.25_{10}\)
5. Describe the following database features(2mks)
(i) Macros
A feature used to automate frequently performed procedures.
(ii) Programming module
It is a feature which automates more complex operations that cannot be achieved using the macros.
6. Describe two ways of creating text in a Microsoft Publisher. (2mks)
Using text tool –Ms-publisher provide a text box which act as text tool
Using text frame- by using text frame or by converting any object created with drawing tool except the line.
7. (a) The formula =M30+Q20 was typed in cell R15 and then copied to cell M24 of a spreadsheet. Write the formula as it appears in cell M24. (2mks)
=H39+L29
(b) Briefly explain the following terms as used in spreadsheet. (2mks)
(i) Cell- An intersection between a row and a column
(ii) value- Numbers that can be manipulated mathematically.
8. Study the following pseudo code and answer the questions that follow.
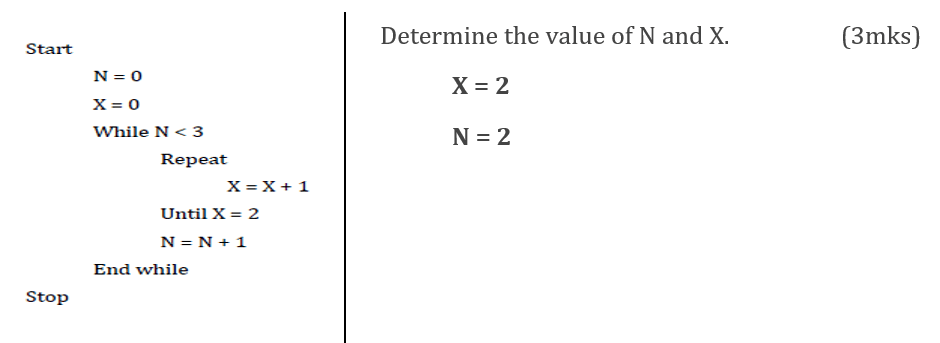
(a) Simplex transmission
Data is transmitted in one direction only.
(b) Half duplex transmission
Data is transmitted in two directions but only in one direction at a time.
10. Explain any two ways in which computers have been made user-friendly for persons that are physically challenged. (2mks)
Use of voice recognition devices for the handicapped
Use Braille
11. Name any four mechanical devices that were used for counting before electronic computers (2mks)
Abacus
Pascaline
Slide rule
Weaving loom
State two ways in which internet enhances business (2mks)
Provides a platform for advertisement of business products
Internet provides convenient means of transaction and EFT
Internet and e-commerce provide convenient way of shopping even for rare products since one does not have to travel to the physical premise
Businesses that are based online have exposure to a worldwide market hence may have high turnover rate
13. Use diagram below to answer question that follows.
(i) Identify the type of operating system represented in Figure 1, 2 and 3 (3marks)
FIG 1- command line
FIG 2-Graphical User Interface
FIG 3- menu driven
(ii) State four advantages of the operating system represented in Figure (2marks)
14. Give two reasons why a company may prefer a tailor made software over vendor-off the shelf software. (2mks)
The solutions it offers give the greatest depth, and flexibility possible in meeting the needs of an organization.
The software developer delivers and installs the software and trains the end users in the use of the new software.
They perform tasks that the general purpose software cannot perform.
This kind of software can be quickly changed when the needs of the organization change, since the source code belongs to the company
15. List four functions of an anti-virus program in a computer (2mks)
Prevent computer virus from attacking computer.
Delete virus from the computer.
Detect the existence
SECTION B(60 MARKS)
ANSWER QUESTION 16 (COMPULSORY) AND ANY OTHER THREE QUESTIONS FROM THIS SECTION
16.(a) Study the flowchart in figure 2 below and use it to answer the questions that follow.
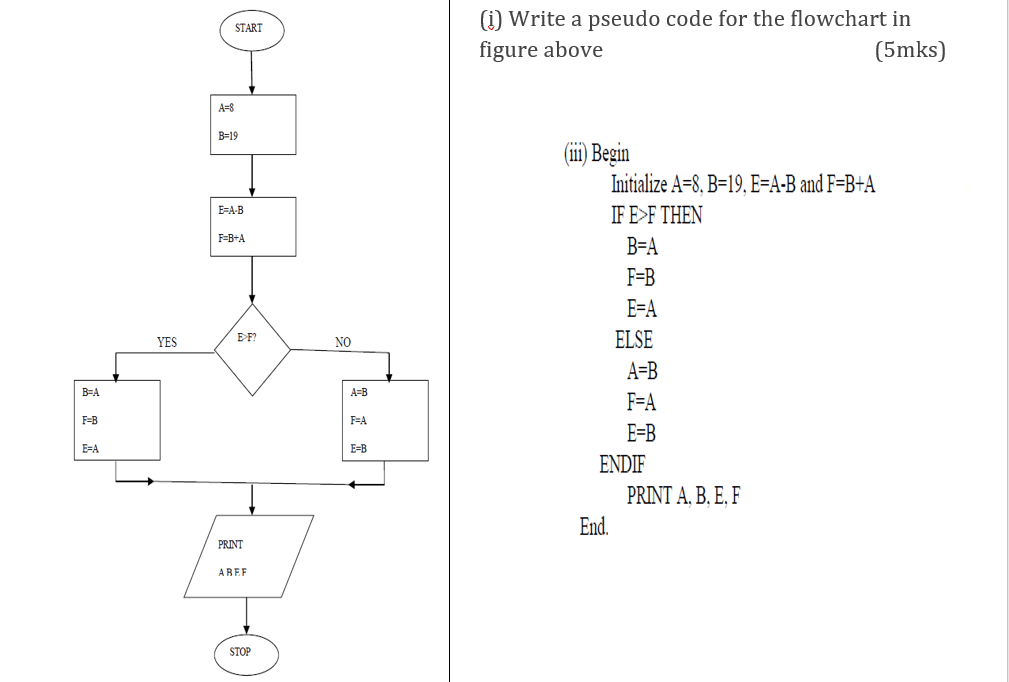
Sequence
Selection
(iii) Determine the value of A, B, C and F.(show your working) (4mks)
A=19, B=19
E=19 and F=19
(b) An airline uses an information system whereby if a passenger at station A books a plane seat, this transaction is immediately shown at stations A and B such that no other passenger can book the same seat.
(i) Name this data processing mode.(1mk)
Real time processing
(ii) State two advantages of this data processing mode. (2mks)
Provides accurate, up-to- date information and hence better services based on a true situation.
It is fast and reliable
Information readily available for instant decision making.
Provides immediate control/ information/feedback.
(c) Explain the following system characteristics(2mks)
(i) System entropy
A system slowly becomes useless to the user either due to improvement in technology, new management policies or change in user requirements
Causes of system entropy
Inadequate testing
Lack of documentation
Changing requirements
(ii) Sub-systems
This means that, a system does not exist alone, but it is composed of subsystems, which are also made up of other subsystems
Is a system that is part of a larger system
17. (a) The diagram below shows a layout of computers networked to access the internet. Use the diagram to answer the questions that follow.
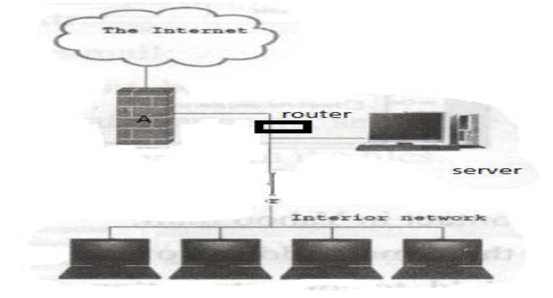
Firewall- a filters some information from the internet
ii. State one two functions of the device labeled server (1mk)
Providing resources to other devices on the network/services requests from clients
iii. Name any two transmission media that can be used to transmit internet to the server. (3mks)
Coaxial cable
Fiber optic
Twisted pair cable
iv. Explain any two challenges that can be faced by interior network user. (2mks)
Security and privacy issues
Spread of malicious software
v. Name the network topology used above (1mk)
star topology
(b) State four roles of a network Administrator. (2mks)
Track network usage and keep a log of people used the network.
Design the network
Secure the network against unauthorized access.
Troubleshoot network related problem.
(c) State any three ways of ensuring efficient back up of data. (3mks)
Making regular backup
Backup on removable media
Keeping backup media in separate location
Setting up automatic backup intervals
(d) State Two advantages of the network topology named in (v) above (2mks)
18. (a) John is a first-year student at JKUAT. He is expected to login his student portal to access online assignments. State three ways in which he would prevent virus from infecting his computer. (3mks)
Scan removable storage devices before use.
Scan email attachments for virus before opening them.
Browse smart.
Install antivirus and update regularly.
(b) Define the following terms. (2mks)
(i) computer fraud
Use of computer to conceal information or cheat other people with the intention of gaining money or information
(i) Industrial espionage
Spying on a competitor to get information that can be used to cripple the competitor
(c) Pesa Company has offices in Nairobi and Kampala connected in a network. The management is convinced that someone is illegally gaining access to the data in their computers. State three ways in which the company can overcome this problem. (3mks)
Encryption.
Firewalls.
User profiles/passwords/user.
Limit the number of log-in attempts.
Audit trail/tracking.
Physical protection of computers
(d) Kagumo High school wanted to setup a network connectivity to be used in school. State three internet connectivity requirements that the school must have to get the connection. (3mks)
Internet Service Provider
Transmission media
Modem
Internet software
Communication node (Computer)
(e)Explain two ways in which the use of internet could make reporting of corruption easier. (4mks)
Interactiveness: the internet based technology enables real-time dialogue hence instantaneous reporting of cases;
Outreach: the technology allows the coverage of wide areas/can be reported from anywhere;
Social mobilisation: It is easy to use technology to create a network with people or organisations with similar concerns;
Anonymity: With use of the technology, it has become easy to report corruption cases without being known;
Security: The message sent reaches the destination with less risk of being intruded.
19. (a) The information in figure 3 below is maintained by the patron of wildlife club in a school. Study it and answer the questions that follow.
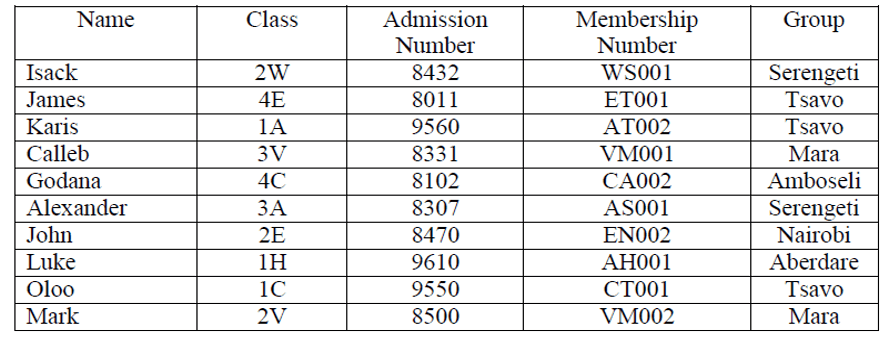
Membership Number
(ii)State the most appropriate data types for the fields (2mks)
(a) Admission number
Number/text
(b) Membership number.
Memo/ Alphanumeric /text
(iii) If a database was to be created for the list; forms, tables, queries and reports are likely to be used. State the purpose of each of these objects. (2mks)
Forms: Are graphical interfaces that resemble an ordinary paper form used to either enter data into or view data from a database. –
Tables: Are database structures organized into rows and columns and used to hold related data
Queries: Are statements used to extract, change, analyze or request for specific data from one or more tables.
Reports: Are summaries generated from underlying tables or queries
(iv) How many field values are in the list? (1mk)
5 fields
(v) How many records are in the list? (1mk)
10 records
(b) A trader uses a spreadsheet program to calculate profits.
The figure below shows the spreadsheet.
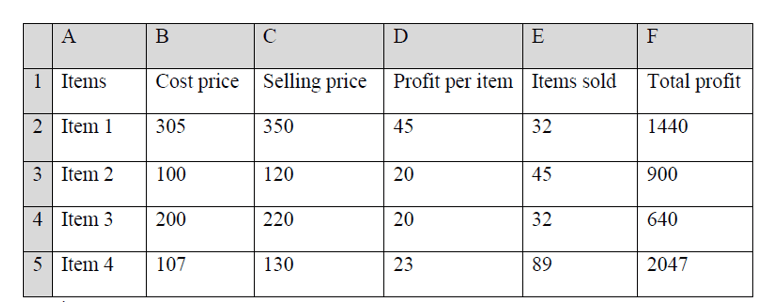
Row 1
(ii) Write the formula that has been entered in cell F2. (2mks)
=Product(D2,E2)
(c)State three features of fifth generation computers. (3mks)
Use of expert system.
Support the use of natural language
Support distributed computing
Support artificial intelligence and voice recognition.
Support parallel processing
Small in size/portable
Superior hardware and software
consume less power
(d) Differentiate between DVD RW and CD R. (2mks)
DVD RW allows data to be written to it, erased and rewritten many times
CD-R allows for recording of data once and does not allow data already written to be erased. Data can only be written in the remaining space
20. a) List four stages of data collection. (4mks)
creation
transmission
preparation
media conversion
input validation
sorting
b) Describe three arithmetic errors that may occur during computerized data processing. (3mks)
Truncation error
Results due, to shortening or leaving out part of a number or a word.
Rounding off error
Arising by approximating a number by replacing it with a number that has fewer significant digits or one with zeros for its ending digits.
Overflow error
Occurs when the results of a computation is larger than the allocated memory space.
Underflow error
Type of error occurs when the output is low small to be represented in the chosen format.
(c)Work out \(32_{10}-19_{10}\) using 8-bit two’s complement(5mks)
Rewrite as \(32_{10} + (-19_{10}\)
Find the binary equivalent of \(19_{10}==00010011_{2}\)
Find the ones complement of \(00010011_{2}=11101100_{2}\)
Add 1 to \(11101100_{2}=11101101_{2}\)
Find the binary of \(32_{10}=00100000_{2}\)
Add \(11101101_{2}\) \(+ 00100000_{2}=(1)00001101_{2}\)
Ignoring the overflow=\(00001101_{2}\)
(d) Work out \(1011101_{2}\) + \(101100_{2}\)-\(1111101_{2}\) (3mks)
\(1011101_{2} \)+ \(101100_{2}\)=\(10001001_{2}\)
\(10001001_{2}\)- \(1111101_{2}\)=\(00001100_{2}\)
