Published on January 12th 2025 | 9 mins , 1682 words
1. Functions of the Control Unit
- Controlling and coordinating the activities of the CPU
- Manages the flow of data within the CPU and between the CPU and other components of the computer system
- Fetches instructions from the main memory
- Interprets instructions fetch from the main memory
- Accepting the next instruction
- Storing the resulting data back in memory
- Sends and receives control signals to and from other components of the computer
2. THREE Factors for Choosing a Desktop Computer's Memory
- Capacity : How much data the memory can hold.
- Speed of access: How fast data can transferred and from the memory
- Cost: What is the cost per gigabyte(GB)?
- Reliability : how long lasting the media is
3. Difference between RAM and ROM (Volatility)
- RAM is volatile while ROM is non-volatile.
- ROM can be read from but written while RAM can both read from and written to
- RAM stores data and instruction that is undergoing processing while ROM stores start-up program (BIOS)
4. When to Format a Hard Disk
- When reinstalling an operating system
- To enhance security before selling, donating or disposing a hard disk or selling one's computer
- To improve performance: Formatting a hard disk can remove malware, viruses, and other harmful content that can slow down a device
- To prepare a new disk for first use
- To fix system errors especially when experiencing frequent operating system errors
5. Measurement Units (Largest to Smallest)
- a) Order: Word, Byte, Nibble, Bit.
- b) Convert 2560 GB to TB: 2560 GB is equal to 2.56 TB.
6. Reasons for Preferring Laser Printers over Dot Matrix Printers
- Speed: Laser printers are faster.
- Quality: They produce clearer, sharper prints.
- Noise: Laser printers are quieter than dot matrix printers.
7. What to Do When the Operating System Becomes Unresponsive (2 actions)
- Restart: Turn off and restart the computer.
- Use Task Manager: End unresponsive programs using Task Manager.
- Press Ctrl+Alt+Del: End the task
7. What to Do When the Operating System Becomes Unresponsive (2 actions)
- Restart: Turn off and restart the computer.
- Use Task Manager: End unresponsive programs using Task Manager.
- Press Ctrl+Alt+Del: End the task
8. Integrity in Data Processing
- Timeliness: Data should be updated and ready when needed.
- Relevance: Data should be useful and related to the task.
12. Word Wrap vs. Wrap Text in Word Processing
- Word Wrap: Text automatically moves to the next line when reaching the margin.
- Wrap Text: Allows text to surround or go around an image or object.
13. Navigation Keys in Spreadsheets (Besides Arrow Keys)
- Tab: Moves to the next cell.
- Enter: Moves down to the next row.
- Home: Moves to the beginning of the row.
14. Stroke vs. Fill in Desktop Publishing
- Stroke: The outline or border around an object.
- Fill: The color or pattern inside an object.
15. Function of a Web Server
- Web Server: Stores websites and delivers them to users when they browse the internet.
16. Source Code Characteristics and Low-Level Programming
Characteristics of Source Code:
- Readable: Written in a language programmers can understand.
- Editable: Can be changed to fix issues or add new features.
- Translatable: Needs to be converted (compiled) to machine code for computers to execute.
Reasons for Choosing Low-Level Programming:
- Speed: Low-level languages are faster for computers to execute.
- Control: Offers more control over hardware and memory.
- Efficiency: Uses fewer resources, ideal for performance-critical tasks.
17a). THREE FACTORS FOR CREATING USER FORMS DURING SYSTEM DEVELOPMENT
- Ease of Use: Should be simple for users to navigate.
- Relevance: Only include necessary information.
- Appearance: Design should be visually clear and organized.
b) Two Benefits of carrying out unit testing during system development
Unit testing is a software testing process in which individual components or modules of a system are tested in isolation to ensure that they work as expected. It is typically performed during the development phase to verify that each unit of the code (e.g., a function, method, or class) operates correctly.
b). Unit Testing Benefits and User Manual Uses
b). Unit Testing Benefits and User Manual Uses
- Benefits of Unit Testing:
- Identifies Bugs: Finds issues early in development.
- Improves Quality: Ensures each part works as expected.
c). Uses of a User Manual:
* 3. Guides New Users: Helps users learn how to use the system. * 4. Solves Problems: Provides troubleshooting steps for common issues.
d). GUI Operations Over Command Line:
* 5. Click and Drag: Move items with the mouse. * 6. Icons: Use icons to open programs. * 7. Windows: Open multiple windows for multitasking. * 8. Menus: Access options using dropdown menus.
18 a). Four advantages the school would gain from installation of an email software
Improved Communication:
- Enables instant communication between teachers, students, parents, and administrators.
- Facilitates timely updates on school events, announcements, and emergencies.
Cost Savings and Eco-Friendliness:
- Reduces costs associated with printing, paper, and postal services.
- Promotes an environmentally friendly approach by minimizing paper use.
Efficient Record Keeping:
- Offers a centralized system for storing and retrieving past communications.
- Ensures important records, such as meeting minutes and student progress reports, are easily accessible.
Collaboration Tools:
- Encourages teamwork through shared email threads, attachments, and collaborative features.
- Helps teachers and staff organize meetings, share documents, and coordinate activities.
Parental Engagement:
- Keeps parents informed about their child’s progress, attendance, and school updates.
- Builds stronger relationships between the school and parents through regular communication.
Enhanced Security and Privacy:
- Provides secure communication channels to share sensitive information, such as grades or disciplinary actions.
- Reduces the risk of information loss compared to physical copies.
b). A database table has fields, EmployeeID, Employee Name, Hours Worked and Rate_Per_Hour. Write an expression that would return:
i) a field name wages which is a product of hours worked and rate per hour (3 Marks)
Wages: [Hours Worked] * [Rate Per Hour]
ii) details of employees whose EmployeeID is between 100 and 200 (2 marks)
BETWEEN 100 AND 200
Here is the transcribed text from the image:
(i). Explain the term data encryption as used in data security (2 marks)
Data encryption means changing information into a secret code so that only people with the correct password or key can read it. It protects data from being seen or stolen by unauthorized people. For example, when you send a message online, encryption scrambles it so only the receiver can understand it.ORData encryption is the process of converting readable data (plaintext) into a scrambled format (ciphertext) before sending it over a network. This ensures that even if someone intercepts the data, they cannot understand it without the decryption key.
(iii) With the aid of an illustration, explain the process of data encryption during transmission of data (4 Marks)
The sender uses an encryption algorithm and a key to convert plaintext (original data) into ciphertext (scrambled data).Example: A message "Hello" becomes "Xy2@#".The receiver uses a decryption key to convert the ciphertext back into plaintext.Example: "Xy2@#" is decoded back to "Hello".
If you have another image you'd like me to transcribe, feel free to share it!
19 a). Web Development Skills and Data Encryption
- Web Development Skills:
- HTML/CSS: For creating web pages.
- JavaScript: Adds interactivity to websites.
- Backend Development: Manages data and server logic.
- Data Encryption: The process of converting information into code to protect it from unauthorized access.
b). Using one's complement convert the decimal number 19.625 to its binary number equivalent
Step 1: Convert the integer part (19) to binary
- Divide 19 by 2 repeatedly, noting the remainders:
- 19 ÷ 2 = 9 remainder 1
- 9 ÷ 2 = 4 remainder 1
- 4 ÷ 2 = 2 remainder 0
- 2 ÷ 2 = 1 remainder 0
- 1 ÷ 2 = 0 remainder 1
Step 1: Convert the integer part (19) to binary
- Divide 19 by 2 repeatedly, noting the remainders:
- 19 ÷ 2 = 9 remainder 1
- 9 ÷ 2 = 4 remainder 1
- 4 ÷ 2 = 2 remainder 0
- 2 ÷ 2 = 1 remainder 0
- 1 ÷ 2 = 0 remainder 1
Write the remainders from bottom to top: 1910 = 100112
Step 2: Convert the fractional part (0.625) to binary
- Multiply the fractional part (0.625) by 2, noting the integer part of the result:
- 0.625 × 2 = 1.25 → Integer part = 1
- 0.25 × 2 = 0.50 → Integer part = 0
- 0.5 × 2 = 1.00 → Integer part = 1
Stop when the fractional part becomes 0.
Combine the results: 0.62510 = 0.1012
Step 3: Combine the integer and fractional parts
Combine the binary results of the integer and fractional parts:
19.62510 = 10011.1012
Many e-waste components, such as batteries, circuit boards, and screens, contain hazardous chemicals like lead, mercury, and cadmium. If not disposed of properly, these can leak into the environment, contaminating the soil, water, and air in and around your home.
Health Risks:
Exposure to toxic substances from e-waste can pose serious health risks. For example, lead can cause neurological damage, while mercury exposure can harm the kidneys and nervous system. Children and pregnant women are particularly vulnerable to these effects.
Air Quality:
When e-waste is burned improperly, such as in informal recycling practices, it releases harmful fumes and particles into the air. This can degrade indoor air quality and lead to respiratory problems.
Fire Hazard:
E-waste, especially items containing lithium batteries, can catch fire if damaged or improperly disposed of. This can increase the risk of home fires.
Space and Clutter:
Accumulation of e-waste in homes can lead to clutter and make living spaces less organized. Old electronics can take up valuable storage space, making it harder to keep the home neat and functional.
Electronic Waste Pollution:
When e-waste is improperly discarded, it can end up in landfills, contributing to pollution. Some e-waste is also exported to developing countries, where it is often processed in unsafe conditions, leading to environmental damage.
Impact on Wildlife:
Toxic chemicals from e-waste can contaminate local ecosystems if they are improperly disposed of. Over time, this can impact local wildlife and the food chain.
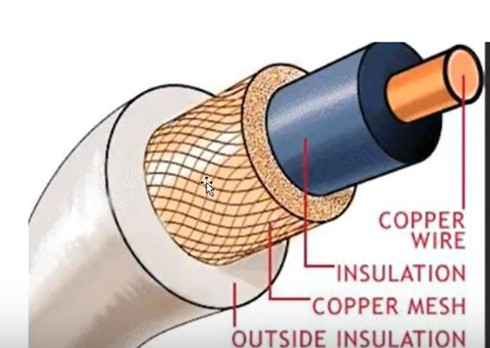
Identify the cable above
Coaxial cable
Advantages
Here are the advantages of using coaxial cable:
- High Bandwidth: Coaxial cables can carry a large amount of data, making them suitable for high-speed internet, cable TV, and other data transmission needs.
- Durability: Coaxial cables are built with durable insulation and shielding, protecting the inner conductors from physical damage, interference, and environmental factors.
- Resistance to Electromagnetic Interference (EMI): The shielding in coaxial cables helps reduce electromagnetic interference, which is ideal for environments with high electrical noise.
- Long Transmission Distances: Coaxial cables can transmit data over relatively long distances (up to several kilometers) without significant signal degradation.
- Relatively Low Cost: Coaxial cables are generally more affordable than fiber-optic cables, making them a cost-effective solution for many applications.