Published on October 18th 2025 | 10 mins , 1862 words
MASENO MOCK
451/1 COMPUTER STUDIES Paper 1
MARKING SCHEME
July 2025 – Time: 2 hours 30 mins
SECTION A: 40 MARKS
1. State two reasons for the increased use of Laptop computers in modern workplaces (2marks)
o Portability
o Have inbuilt batteries and therefore can store power
o They’re designed with an improved technology hence more efficient
2. What precautions would you take in the computer laboratory incase users are complaining of overheating and suffocation. (2marks)
o Ensure all doors and windows are open while the lab is in use
o Installing fans
3. Define the term phishing and explain how it poses threat to computer users (3marks)
Phishing refers to a form of cyber attack that uses fraudulent emails, text messages, phone calls or websites to trick people into sharing sensitive data. During these scams, the attacker will pose as a trusted contact to steal data like logins, account numbers etc
4. List any three types of security threats that organisations face when using networked computer systems (3marks)
o Malware
o Viruses
o Worms
o Spyware
o Phishing
5. State three circumstances which may force an individual to acquire an impact printer instead of non-impact printer. (3marks)
o When an individual has less money and therefore can’t afford non-impact printers
o When the output required is of low quality
o When there’s need for multiple copies in one instance of print
6. Sam prepared a five-page brochure of Maseno School using Ms-publisher. He wanted to insert a school badge in each page of the publication. State two methods he need to apply to execute this task. (2marks)
o Inserting as a header/footer
o Creating a master page
7. Javan Joe has recently secured a job at maseno university as a database administrator. Outline two roles Joe will be expected to perform. (2marks)
o Designing and developing database systems
o Enforcing security measures needed to control access to data and information.
o Maintaining the databse by adding new records, modifying or deleting unnecessary records.
8. Explain the impact of Information Technology on organization in each of the following areas. (2 marks)
(a) Employment
o Job replacement
o Job displacement
o Job creation
(b) Environment
o Energy consumption
o Environmental pollution
9.State four benefits of cloud storage in computing. (4marks)
o Easy accessibility to information
o High level of security and data protection
o Saves on cost
o Facilitates easy file sharing
o Can be used as back up in case physical storage is damaged
10. Describe the functions of the following disk management operations.
(a) Defragmentation (1mark)
The process of moving file fragments to contiguous location to optimize on storage space
(b) Partitioning (1mark)
o The process of subdividing a large physical storage media into two or more partitions called logical drives.
11. State four ways through which an organization can minimize threats to its data integrity. (4marks)
o Back up data preferably on external storage media
o Control access to data by enforcing security measures
o Design interfaces that minimize chances of invalid data entry
o Using error detection and correction softwares
o Using devices that directly capture data from the source
12. Give three reasons why people prefer in-house developed application programs to general-purpose application packages. (3marks)
o Ability to tailor the software to specific organizational needs
o It is easier and faster to make any changes/modifications
o Ensures complete ownership of the software including the source code
13. State any three page formatting features in word processors (3marks)
o Margins
o Paper size
o Orientation
o Borders
o Headers and footers
o Columns
o Page numbering
14. Five students Jane, Beryl, Baroness, Linda, and Jael scored the following marks in mathematics: 45, 76, 34, 65 and 45. The marks were recorded in cell C3 to C7. Write down the most appropriate function that can be used to give positions so that they can be awarded in descending order. (3marks)
o =RANK(C3, $C$3:$C$7,0)
15. List TWO human features used by Biometric systems installed in a computer to authenticate users (2 marks)
o Finger print
o Face
o Voice
o Iris and retina
o Hand geometry
SECTION B: (60 MARKS) ANSWER QUESTION NUMBER 16 ANY OTHER THREE QUESTIONS FROM THIS SECTION
16. (i) Define the following terms as used in programming.
(a) Structured/procedural language (3marks)
o A programming language makes it possible to break a program into smaller components called modules each performing a particular task.
(b) Debugging
o Refers to the process of correcting errors in a program
(c) Syntax
o Refers to a special sequence or order of writing characters in a given programming language
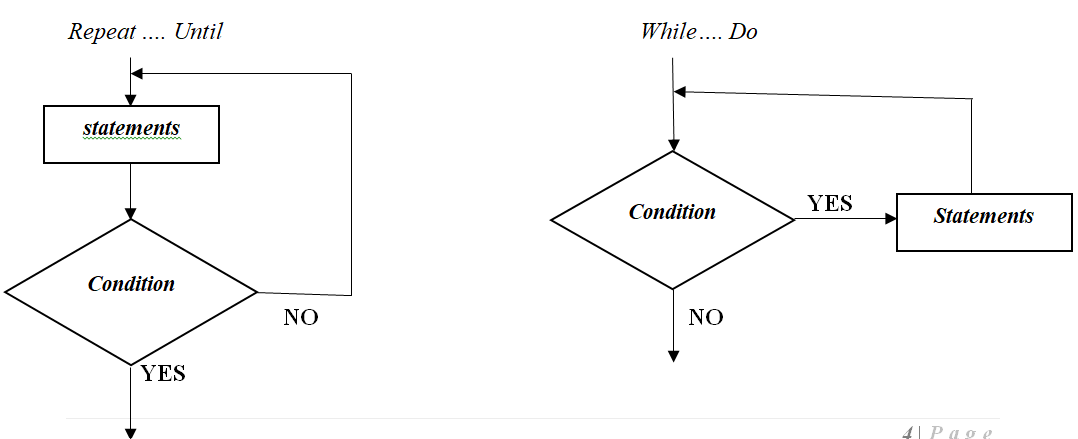
(ii) With an aid of a diagram differentiate between Repeat Until and While… Do loops. (4 marks)
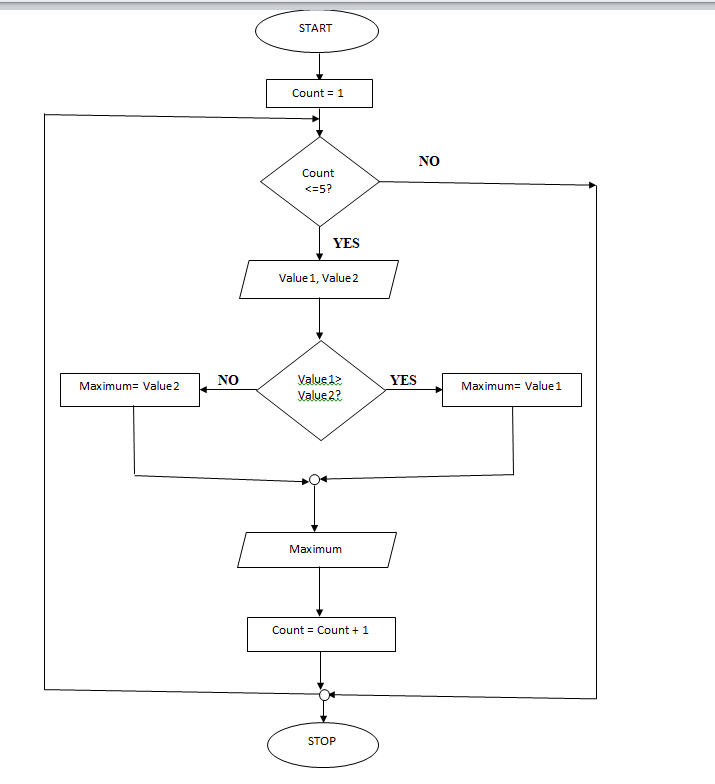
(iv)Study the pseudo code below and design its equivalent flowchart (8marks)
17. (i) The five-bit number 001012 is used to represent decimal number 5, show three methods of coding for negative 5. (3marks)
o Prefixing a sign bit: (1)001012
o One’s complement: 110102
o Twos complement: 110112
(ii) Convert the binary number 1010111101011011100012 into its
(a) Octal equivalent (2marks)
o \(101 011 110 101 101 110 001_{2}\)
= \(5365561_{8}\)
(b) Hexadecimal (2marks)
o \(0001 0101 1110 1011 0111 0001_{2}\)
= \(15EB71_{16}\) / 15EB71H
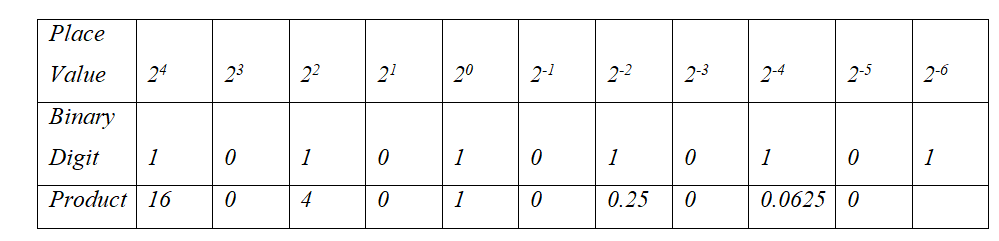
(iii) Convert 10101.0101012 to decimal (3marks)
=16+4+1+0.25+0.0625+0.015625= \(21.3281255_{10}\)
(iv) Use 8-bit twos to subtract \(35_{10}\) from \(17_{10}\) (3marks)
\(17_{10}\) + \(-35_{10})\)
\(17_{10}\) = \(00010001_{2}\)
\(35_{10}\) = \(00100011_{2}\)
1s complement of \(00100011_{2}\) = \(11011100_{2}\)
2s complement = \(0011101_{2}\)
Adding \(00010001_{2}\) + \(0011101_{2}\) = \(11101110_{2}\)
(v) Perform the following calculation: \(110001_{2}\) + \(1111_{2}\) - \(11111_{2 }\) (2marks)
o \(110001_{2}\) + \(1111_{2}\) = \(1000000_{2}\)
o \(1000000_{2}\) - \(11111_{2}\) = \(00001_{2}\)
18. (i) Define the term desktop publishing. (2marks)
o Refers to the process of designing publication using a desktop publishing software
(ii) List three nonprinting guides used in Desktop publishing (3marks)
o Ruler guides
o Column guides
o Margin guides
(iii) Differentiate between fill and stroke as used in DTP (2mks)
o Fill refers to the interior color, pattern or gradient applied to the inside of a shape while stroke refers to the outline border of the shape
(vi) Describe any three types of action queries. (3marks)
o Update
o Append
o Make table
o Delete (with relevant explanation)
(iv) Describe the function of the following features of a query grid.
(a) Criteria (1mark)
o This is where you enter a condition or expression that will be used by the query to filter records
(b) Show (1mark)
o Specifies whether to display the fields in the query results/dynaset
(v) Mention three functions of database management software. (3mks)
o Allows authorized users to add or delete records
o Allows users to to update or modify existing records
o Organizes files and records for easy access, retrieval and sharing
o Acts as an interface between the database and other application programs
o Ensures security and integrity of data
19. (i) State the stage of system development life cycle in which each of the following activities take place (3mks)
a) Determination of the cost effectiveness of a system
o Analysis
b) Interviews
o Information gathering/ fact finding
c) Staff are trained
o Implementation
(ii) Outline any three ways in which an organization may switch from an old system to a new one (3mks)
o Direct/Straight
o Phased
o Parallel
b) The following are some of the phases in the systems development life cycle (SDLC): system analysis, system design, system implementation, system review and maintenance. State three activities that are carried out during the system implementation phase (4mks)
o File conversion
o Staff training
o Change management/change over
c) Give three reasons why system maintenance phase is necessary in SDLC (3mks)
o To ensure optimal performance
o To enhance security
o Prevents system entropy
o Reduces the risk of system failure
d) State two instances where observation is not a viable method of gathering information during system analysis stage (2mks)
o When the analyst wants to gather confidential information
o When information is to be gathered from a large audience
o Time constraints
20. Study the diagram below and answer the questions that follow.
(a) (i) Name the above cable as used in data communication media (1mk)
o Coaxial cable
(ii) Name the parts labeled A, B, C and D (4mks)
o A- Copper Core
o B- Dielectric material
o C-Metallic Foil
o D-Meshed Alluminium Earthing
(iii) Highlight any Three advantages of the above cable. (3mks)
o Stable even under high transmission volumes
o Have a higher bandwidth
o Can carry voice, data and video signals simultaneously
o Resistant to radio and electromagnetic interference
(b) With the aid of a diagram, distinguish between star topology and ring topology giving one disadvantage of each. (4mks)
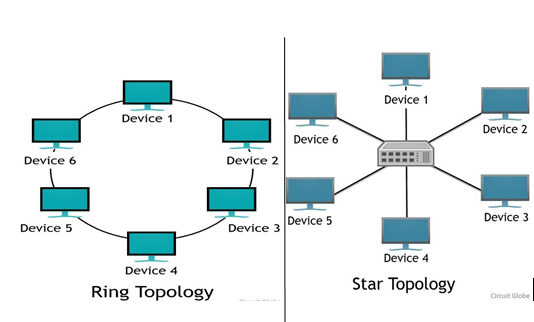
Disadvantages
Ring:
o Modification may be difficult
o Troubleshooting can be difficult
o Device or media breakdown may affect the entire network
Star
o Costly
o If the central hub fails, the entire network breaks down
o Installation is time consuming
(c) List any three data communication devices used in networking (3mks)
o Network interface adapter
o Modem
o Network hub
o Switch
o Bridge
o Repeater
o Router
o Gateway