Published on February 22nd 2025 | 10 mins , 1913 words
- USB support connection of many devices ✔
- USB Interface support fast data transmission ✔
- USB Connection provide quality transmission ✔ (Award 1 mark each Max 2)
2. State three methods of input available for the operation of a smartphone. (3 marks)
- Voice Input ✔
- Touch screen ✔
- Finger Print Scanning ✔
- QR code scanning ✔ (Award 1 mark each Max 3)
3. A vehicle assembly company has introduced robots to replace the human workforce. Describe two effects this would have on the work force. (2 marks)
- Job creation – for the skilled personnel who will operate the robots ✔
- Job replacement – Robot will take up the jobs of unskilled human resource causing unemployment ✔ (Award 1 mark each Max 2)
- Job displacement – Some unskilled human resource will be transferred to some section or department within the big mechanism (Descriptive but okay)
4. (i) It was noted that after every lesson, the students complained of itchy eyes and mild headache. State any two reasons for this problem. (2 marks)
- Very bright monitors – Monitors facing the windows ✔
- Flickering screen/Monitor ✔ (Award 1 mark each Max 2)
- Poor lighting in the room ✔
(ii) State any two solutions to the problem mentioned in (4)(i) above. (2 marks)
- Adjust the screen brightness and contrast ✔
- Avoid using flickering monitors ✔ (Award 1 mark each Max 2)
- Consider using anti-glare screens ✔
- Computer screens should face away from the windows ✔
- Consider new quality screens ✔
- Consider use of dark colored background ✔
- Consider regular breaks ✔
5. State any two importance of referential integrity with reference to database tables. (2 marks)
- It ensures all data in a database remain consistent and up to date ✔ (Award 1 mark each Max 2)
- It helps to prevent incorrect records from being added, edited, or modified ✔ (Accept similar answers)
6. State ways of manipulating text in a printable area of a publication. (2 marks)
- Using text box ✔
- Using text frame ✔ (Award 1 mark each Max 2)
7. Bradwil is pursuing a Bachelors of Computer Science at University of Lagos in Nigeria. He is supposed to graduate at the end of this year and then come back to Kenya to seek for employment. Name any three career opportunities in the field of ICT that Bradwil may take up after graduation. (3 marks)
- Computer Programmer ✔
- System Analyst ✔
- Database Administrator ✔ (Rule: Accept related professions)
- Network Administrator ✔ (Award 1 mark each Max 3)
8. Malcom limited designs and sells software to end users in different parts of the country. The company noticed that some end users make copies of their products and selling without their permission to some users at a lower rate. State three things that the company can do to stop this malpractice. (3 marks)
- Make software price affordable ✔
- Use product codes/labels to prevent illegal installations ✔
- Use licenses and certificates to identify genuine software ✔
- Enforce the law that protects the owners of data and information ✔ (Award 1 mark each Max 3)
9. Explain three hardware factors that one must consider before installing an operating system. (3 marks)
- Memory space – There are operating systems that require a large memory space before they can be installed ✔
- Hard disk capacity – The OS will need space to be installed and store data ✔
- Processor speed – A slow computer should have a suitable operating system ✔
- Screen and disk type – To accommodate the OS and its associated data ✔
- Processor type – Modern OS require fast speed processors and most will not work on very slow processors ✔
- Display resolution – Ensure compatibility with screen resolution ✔ (Award 1 mark each Max 3)
10. Financial institution handles a lot of data and also collaborate with other companies all over the World and therefore data integrity must be maintained at all times. Describe three ways employed by modern financial institutions to minimize threats to its data. (3 marks)
- Use secured channels when transferring data directly from source ✔
- Use error detection and correction when transmitting data ✔
- Design user interfaces that minimize chances of invalid data entry ✔
- Control access to data by enforcing security measures ✔
- Backup data on an external storage media periodically ✔
(Award 1 mark each Max 3)
11. Mr. Kikozi bought a flash disk of 16GB. He used quarter of the total space in the flash to save his personal documents, a half of the remainder for audio files. Calculate the remaining space in the flash in Megabytes. (3 marks)
- Total space = 16GB
- Used space = \(\frac{1}{4} \times 16 = 4 GB \)✔
- Remaining space = 16−4=1216 - 4 = 12 GB
- Used for audio = \(\frac{1}{2} \times 12 = 6 GB \)✔
- Remaining space = 12−6=612 - 6 = 6 GB
- In MB: 6×1024= 6144 MB ✔ (Award 1 mark each step)
12. Explain the function of the following layers of OSI model: (2 marks)
(a) Session layer:
- Responsible for setting up, managing, and terminating communication sessions ✔
(b) Presentation layer:
- Ensures data is in a usable format and handles data encryption and compression ✔
(Award 1 mark each Max 2)
13. Describe two benefits of extensive use of Mobile Banking in modern society. (2 marks)
- The transaction cost is low as compared to other means ✔
- Provides a safe, convenient platform for financial transactions ✔
- Mobile banking saves time and reduces the need for physical presence ✔
- The platform is easily accessible and available for use anytime ✔
(Award 1 mark each Max 2)
14. Describe the term collated as used in printing. (1 mark)
- Refers to arranging printed pages in a specific order ✔
15. Describe three technological platforms used by Kenyan Secondary students to collaborate with their peers in Canada, US, and UK. (3 marks)
- Social media platforms: Students use Facebook, Instagram, and WhatsApp to link with peers and allow them to share educational materials ✔
- Video conference: Through Zoom, Webex, and Google Meet, learners can have discussions in a given learning area ✔
- Email: Enables learners to exchange mails and attach educational materials ✔
- Google Docs: Provides a platform for learners to share documents/sheets online ✔
(Award 1 mark each Max 3)
(Rider: Accept platforms that support collaboration)
SECTION B: 60 MARKS
16.
(i) Mention three attributes of a Machine language. (3 marks)
- Program instructions are in binary form ✔
- Program instructions are machine-dependent ✔
- Program instructions execute very fast ✔ (Avoid 1 mark each, Max 3)
(ii) Explain the following qualities of an Algorithm:
(a) Definiteness (2 marks)
- The algorithm must be clear and detailed in its steps. There is no ambiguity in the steps ✔ (Endorse 1)
(b) Finiteness (2 marks)
- An algorithm must always terminate after a finite number of steps. (Indicate a start and stop) ✔ (Endorse 1)
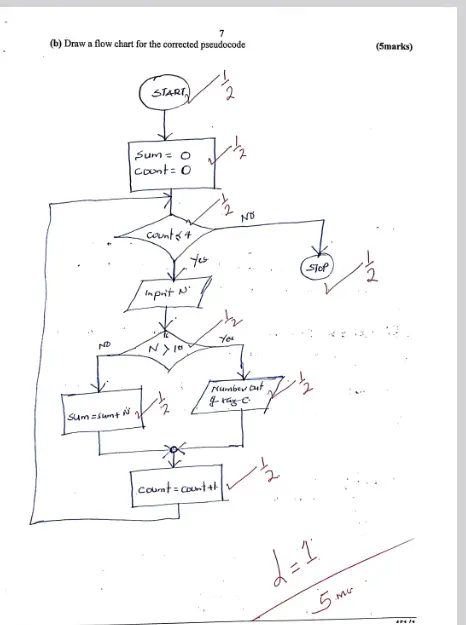
(iii) The pseudocode below was written by a learner. Use it to answer the questions that follow:
START
Sum = 0
Count = 0
For Count = 0 to 5 do
Print "Enter a number"
Input N
If N > 10 then
Number out of range
Else
Sum = Sum + N
End if
End for
Print sum
STOP
(a) Identify the errors in the above pseudocode. (3 marks)
- Initialize Count as Count = 0 ✔
- Condition: For Count = 0 to 4 instead of For Count = 0 to 5 ✔
- The pseudocode lacks the increment, and therefore cannot trace the loop: Count = Count + 1 ✔
- Print sum should be Print N ✔ (Award one for the correct correction in correct statement in pseudocode)
(a) The system analyst walks the users through the system
- System Implementation ✔
(b) A list of hardware and software requirements is generated
- System Requirement Specification ✔
(c) Preparing of test data
- System Construction ✔
(d) The system analyst presents a report recommending a change in the system.
- Feasibility Study ✔ (Award 1 mark each Max 4)
(ii) State the difference between pilot and phase change-over methods. (2 marks)
- Pilot change-over: Involves testing the system on an experimental basis ✔
- Phase change-over: Implementation is done in portions, one part at a time or step by step ✔ (Award 1 mark each Max 2)
(iii) Explain the reason for conducting the following studies in system development (2 marks)
(a) Operational feasibility
- To establish how well users can operate or cope with the proposed or new system ✔
(b) Schedule feasibility
- To establish whether developing the new system or phase will be accomplished within the available time ✔ (Award 1 mark each Max 2)
(iv) Janabi was preparing a document in MS Word which contained both text and graphics. He realized that graphics in the document were not properly fitted. State two ways Janabi can fit the graphics nicely in the document. (3 marks)
- Rotation ✔
- Resizing ✔ (Award 1 mark each Max 3)
(v) Mention three advantages of mail merging (2 marks)
- Helps in generating uniform documents ✔
- Saves time in creating similar documents ✔
- Uses a data source to create many documents simultaneously ✔ (Award 1 mark each Max 2)
18.
(i) Using 8 bits and two’s complement subtract 41₁₀ from 30₁₀, giving your answer in decimal notation (4 marks)
Step-by-step solution provided with bitwise operations:
- 30₁₀ = 00011110₂
- 41₁₀ = 00101001₂
- Two’s complement of 41₁₀: 11010111₂
- Adding: 00011110₂ + 11010111₂ = 11110101₂
- Result: -15₁₀ ✔ (Award 4 marks)
(ii) Arrange the following numbers from the smallest to the largest: 101110₂, A₁₆, 65₁₀, and 320₁₀ (2 marks)
Convert to decimal:
- 101110₂ = 46₁₀
- A₁₆ = 10₁₀
- 65₁₀ = 65₁₀
- 320₁₀ = 320₁₀
Order: A₁₆ (10), 101110₂ (46), 65₁₀ (65), 320₁₀ (320) ✔ (Award 2 marks)
(iii) Convert ACF₁₆ to binary number system (2 marks)
- A₁₆ = 1010₂, C₁₆ = 1100₂, F₁₆ = 1111₂
- ACF₁₆ = 1010 1100 1111₂ ✔ (Award 2 marks)
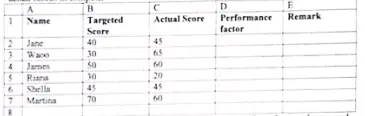
(iv) The table below is an extract of a spreadsheet showing what the students had targeted and the actual scores in computer:
Name Targeted Actual Score Performance Factor Remark
(a) Write a formula that uses cell references only to compute the performance factor (2 marks)
- =C2/B2 ✔ (Award 2 marks)
(b) Write a formula to determine the best performance factor (2 marks)
- =MAX(C2:C6) ✔ (Award 2 marks)
(c) E2 to display remarks:
- If factor < 1 → "More Remedial"
- If factor = 1 → "Exempted"
- Otherwise → "Optional remedial"
Formula:
=IF(D2<1,"More Remedial",IF(D2=1,"Exempted","Optional remedial")) ✔ (Award 3 marks)
✅ Awarding criteria:
- Formula name = 1 mark
- Correct brackets = 2 marks
19. (i) Briefly describe two functions of a query as used in a database (2 marks)
- Search for specific data items in the database ✔
- Delete, change, and add items to a table ✔
(Award 1 mark each, max 2 marks)
(ii) Explain the following features of a DBMS (4 marks)
(a) Macro (2 marks)
- A set of database objects that automates frequently performed tasks. ✔ (Award 2 marks)
(b) Module (2 marks)
- A built-in programming environment used to automate database operations. ✔ (Award 2 marks)
(iii) Describe two types of control used when designing a form as a user interface in a database (2 marks)
- Bound Control – Linked to a data source like a field in a table. ✔
- Unbound Control – Not linked to any data source; used for labels or images. ✔
(Award 1 mark each, max 2 marks)
(iv) A student created a relationship between two tables but the query was invalid due to a Type Mismatch error.
(a) State the cause of this error (1 mark)
- Data types of the linked fields are different. ✔ (Award 1 mark)
(b) State how this error can be corrected (2 marks)
- Open the tables in design view and change the field data types to be the same. ✔ (Award 2 marks)
(v) What is telecommuting? (2 marks)
- Working from home and communicating with the workplace through technology like computers, telephones, and the internet. ✔ (Award 2 marks)
(vi) Give two reasons to justify why telecommuting is gaining popularity in the modern workplace (2 marks)
- Flexible working hours ✔
- Reduces overall costs (e.g., commuting and office expenses) ✔
(Award 1 mark each, max 2 marks)
20. (a) Explain the following terms as used in Data security
(i) Vulnerability
is a weakness, flaws or error found within a computer (2marks)
has the potential to be leveraged by a threat agent in order to compromise a security network.
(ii) Social engineering
-is a threat to data and information where people unknowingly give out information to strangers or unauthorized persons.
-The act of soliciting for sensitive information from unsuspecting users
(b) State two example of security monitors used to control threats to data (2marks)
-Log files/ audit trails
(c) Alteration is illegal changing of data and information. This is one of the computer crimes common in the 21" Century. Describe three ways employed by organizations to curb this vice (3marks)
-Assign users access rights
-Install CCTV Cameras to Monitor the computer.
-Motivate the employees
-Security policies
-Use of log files
(d) Kijawinni runs a learning Institution in Kenya. List three top level domain names that he can use when creating a website (3marks)
• ac
• edu
• sc
(e) Mention three communication based internet services (3marks)
• Social Media
• Website
• Instant Messaging
• Newsgroups